scrollcaps, i may “rant”, incoherently so, but im spitting them facts, whether one likes it or not
FredTheFeline, sorry, i was on a long suburban stroll while my account was apparently “suspended” for “toxic behaviour” (hilarious, i know  ), but um, anyway, uh, a couple of things that i want to point out:
), but um, anyway, uh, a couple of things that i want to point out:
distrobox create --name fedora --init --image fedora:latest
sometimes may download a faulty, broken init, which will spit an error:
Firing up init system...
Error: could not set up init system, no init found!
Consider using an image that ships with an init system,
or add it with "--additional-packages" during creation.!
that’s annoying. but there is a solution. so, two things:
- forget the
--init flag. dont worry about it.
- because
fedora:stable is not a real tag, which can be seen here, use fedora:41 instead (the one that you’re using).
distrobox create --name fedora --image fedora:41
it may still scream with:
Image fedora:41 not found.
Do you want to pull the image now? [Y/n]: y
ignore it. it is an alias. it will still pull the correct image.
so, that’s how you fix this issue, if anyone’s wondering.
remember, you can always wipe your containers and start again with:
podman system reset
…
anyway, now that we (well, just me, actually, because nixOS is a tad bit wacky sometimes) got this out of the way, i had a look at your problem… but first, i had to do everything again from scratch. here i am with a fresh, new fedora 41, wanting to compile and play beamMP… but i got the same error as you!
CMake Error at /home/user/Downloads/vcpkg/scripts/buildsystems/vcpkg.cmake:941 (message):
vcpkg install failed. See logs for more information:
/home/user/Downloads/BeamMP-Launcher/bin/vcpkg-manifest-install.log
Call Stack (most recent call first):
/usr/share/cmake/Modules/CMakeDetermineSystem.cmake:146 (include)
CMakeLists.txt:3 (project)
CMake Error: CMake was unable to find a build program corresponding to "Unix Makefiles". CMAKE_MAKE_PROGRAM is not set. You probably need to select a different build tool.
CMake Error: CMAKE_C_COMPILER not set, after EnableLanguage
CMake Error: CMAKE_CXX_COMPILER not set, after EnableLanguage
-- Configuring incomplete, errors occurred!
but then i looked closer. openssl (as a dependancy of BeamMP-Launcher) wanted linux-headers, which fedora in this container doesnt have. but there is no such package named linux-headers in fedora, however, there is a kernel-devel package… but then, there were other hints, such as missing perl-IPC-Cmd and perl-FindBin. i was getting closer, the error kept changing. how about i download the whole perl metapackage (~200 packages)? and it ■■■■■■■ worked, mate! NO variable setting required! here’s how to reproduce:
sudo dnf install @development-tools git cmake g++ perl openssl
(shortly after this the full list of dependancies for fedora was added here)
cd Downloads
git clone https://github.com/microsoft/vcpkg.git
cd vcpkg
export VCPKG_FORCE_SYSTEM_BINARIES=1
(this variable may not be required… but i was testing things… set this before bootstrapping)
./bootstrap-vcpkg.sh --disableMetrics
cd ..
git clone https://github.com/BeamMP/BeamMP-Launcher.git
cd BeamMP-Launcher
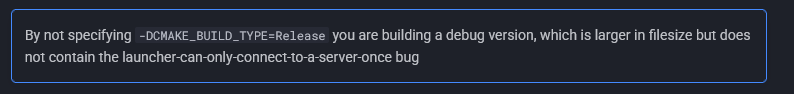
cmake -DCMAKE_BUILD_TYPE=Release . -B bin -DCMAKE_TOOLCHAIN_FILE="~/Downloads/vcpkg/scripts/buildsystems/vcpkg.cmake" -DVCPKG_TARGET_TRIPLET=x64-linux
(once again, we are using a -DCMAKE_TOOLCHAIN_FILE= because it just works and is reproducible. if you want to use an absolute path to your system’s compiler - go ahead)
cmake --build bin --parallel --config Release
cd bin
strip BeamMP-Launcher
(you can also get gamemode (Github) to launch with improved performance)
and that’s it! i was THIS close to giving up. it was INSANE. i was about to spam the devs that their CMakeLists.txt is ■■■■■■ or something
also i have no ■■■■■■■ clue why it needs perl, perhaps because it also downloads C related dependancies?
…next time, please, just use another ■■■■■■■ distro, alright? 

tl;dr:
sudo dnf install @development-tools git glibc cmake make gcc g++ kernel-devel perl openssl nss
(just to be safe, there is everything!)
(these are ONLY to COMPILE the BeamMP-Launcher! NOT to LAUNCH the BeamNG.drive.x64 game binary! for the game’s dependancies, see this comment.)
TODO: edit my previous “tutorials”… for anyone reading, i am, too, just a learner. im not big into computers. if anything, i hate digitalisation. so lower your expectations from me